BIOMETRICS
Biometrics
is the technique of the identification and authentication of the digital
signature. This will assure the security in the accessing of information that
uses physical and logical access control.
A bio metrical factor is a behavior or physiological characteristics of unique to
a subject as a biometric factor is used instead of the username or account ID
as an identifier requires a one-to-many search
There
are many types of biometric factors
Finger print
Face Scans
Iris Scans
Retina Scans
Palm Scans
Heart/Pulse patterns
Voice patterns
Signature dyamics
Keystroke Pattern
A biometric device must be able
to read information that is very minute, such as the variations in then blood
vessels in a person’s retina or the tones and timbres in their voice. This is
mostly preferred such as most people are basically similar, the level of detail
required to authenticate a subject often results in false negative and false
positive authentications.
Biometric devices are rated for
their performance against these two negative authentication conditions. Most
biometric devices have a sensitivity adjustment so they can be tuned to
be more or less sensitive.
When a biometric device is too
sensitive, a Type 1 error occurs. A Type 1 error occurs when a valid
subject is not authenticated. The ratio of Type 1 errors to valid authentications
is known as the False Rejection Rate (FRR).
When a biometric device is not
sensitive enough, a Type 2 error occurs. A Type 2 error occurs when an
invalid subject is authenticated. The ratio of Type 2 errors to valid authentications
is known as the False Acceptance Rate (FAR).
The FRR and FAR are usually
plotted on a graph that shows the level of sensitivity adjustment against the
percentage of FRR and FAR errors.
The point at which the FRR and FAR are equal
is known as the Crossover Error Rate (CER).
The CER level is used as a
standard assessment point from which to measure the performance of a biometric
device. In some situations, having a device more sensitive than the CER rate is
preferred, such as with a metal detector at an airport.
For a biometric device to
function as identification or an authentication mechanism, the subject must be enrolled
or registered. This means the subject’s biometric must be sampled and stored in
the device’s database. The time required to scan and store a biometric varies
greatly by what physical or performance characteristic is used. The longer it
takes to enroll with a biometric mechanism, the less a user community accepts
the inconvenience. In general, enrollment times longer than two minutes are
unacceptable. If a biometric characteristic that changes with time is used,
such as a person’s voice tones, facial hair, or signature pattern, enrollment
must be repeated at regular intervals.
ACCOUNTABILITY
AND ACCESS CONTROL
Once subjects are enrolled, the
amount of time the system requires scanning and process a subject is the throughput
rate. The more complex or detailed the biometric characteristic, the longer
the processing time will take. Subjects typically accept a throughput rate of
about six seconds or faster.
A subject’s acceptance of a
security mechanism is dependent upon many subjective perceptions, including
privacy and psychological and physical discomfort.
Subjects may be concerned about
transfer of body fluids or revelations of health issues via the biometric
scanning devices.
TOKENS
Tokens are password-generating
devices that subjects must carry with them. Token devices are a form of
“something you have.” A token can be a static password device, such as an ATM
card. To use an ATM card, you must supply the token (the ATM card itself) and you’re
PIN. Tokens can also be one-time or dynamic password devices that look a bit
like small calculators.
The device displays a string of
characters (a password) for you to enter into the system.
There are four types of token
devices:
_ Static tokens
_ Synchronous dynamic password
tokens
_ Asynchronous dynamic password
tokens
_ Challenge-response tokens
STATIC
TOKENS
A static token can be a swipe card, a smart card, a floppy
disk, a USB RAM dongle, or even something as simple as a key to operate a
physical lock. Static tokens offer a physical means to provide identity. Static
tokens still require an additional factor to provide authentication, such as a
password or biometric. Most device static tokens host a cryptographic key, such
as a private key, digital signature, or encrypted logon credentials. The cryptographic
key can be used as an identifier or as an authentication mechanism.
The cryptographic key is much
stronger than a password because it is pre-encrypted using a strong encryption
protocol, it is significantly longer, and it resides only in the token. Static
tokens are most often used as identification devices rather than as
authentication factors.
SYNCHRONOUS
DYNAMIC PASSWORD TOKEN
A synchronous dynamic password token generates passwords at
fixed time intervals. Time interval tokens require that the clock on the
authentication server and the clock on the token device be synchronized.
The generated password is entered
into the system by the subject along with a PIN, pass phrase, or password.
The generated password provides
the identification, and the PIN/password provides the authentication.
ASYNCHRONOUS
DYNAMIC PASSWORD TOKEN
An asynchronous dynamic password token generates passwords
based on the occurrence of an event. An event token requires that the subject
press a key on the token and on the authentication server.
This action advances to the next
password value. The generated password and the subject’s PIN, pass phrase, or
password are entered into the system for authentication.
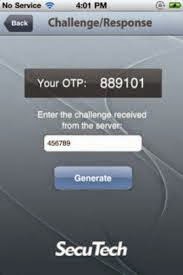
CHALLENGE RESPONSE TOKENS
Challenge-response
tokens generate
passwords or responses based on instructions from the authentication system.
The authentication system displays a challenge, usually in the form of a code
or pass phrase. This challenge is entered into the token device. The token
generates a response based on the challenge, and then the response is entered
into the system for authentication.
Token authentication systems are
much stronger security measures than password authentication alone. Token
systems use two or more factors to establish identity and provide
authentication. In addition to knowing the username, password, PIN, code, and
so on, the subject must be in physical possession of the token device.
If the battery dies or the device
is broken, the subject is unable to gain access. Token devices can be lost or stolen.
Tokens should be stored and managed intelligently because once a token system
is compromised, it can be difficult and expensive to replace.
TICKETS
Ticket
authentication
is a mechanism that employs a third-party entity to prove identification and
provide authentication. The most common and well-known ticket system is Kerberos.
The Kerberos authentication
mechanism centers on a trusted server (or servers) that host the functions of
the Key Distribution Center (KDC), the Ticket Granting Service (TGS),
and the Authentication Service (AS). Kerberos uses symmetric key
cryptography to authenticate clients to servers.
All clients and servers are
registered with the KDC, so it maintains the secret keys of all network
members.
SINGLE SIGN ON
Single
Sign On (SSO) is
a mechanism that allows a subject to be authenticated only once on a system.
With SSO, once a subject is authenticated, they can roam the network freely and
access resources and services without being challenged for authentication.
SSO typically allows for stronger
passwords because the subject must memorize only a single password.
SSO offers easier administration by
reducing the number of locations on which an account must be defined for the
subject. SSO can be enabled through authentication systems or through scripts
that provide logon credentials automatically when prompted.
Scripts, Kerberos, SESAME, and
KryptoKnight are
examples of SSO mechanisms.









No comments:
Post a Comment